An attack that hit the NHS brought to light a global ransomware infection, hitting 75,000 computers in 99 countries, demanding ransom payments in 20 languages.
Ransomware is computer malware that installs covertly on a victim’s device that either mounts the cryptoviral extortion attack from cryptovirology that holds the victim’s data hostage, or mounts a cryptovirology leakware attack that threatens to publish the victim’s data, until a ransom is paid.
Yesterday, NHS services across the UK were hit by a large-scale cyber-attack. Hospitals across the country have reported being hit by the attack and in some instances in England, patients are being turned away from A&E and operations are being cancelled.
East and North Hertfordshire NHS trust said in a statement:
“The trust is postponing all non-urgent activity for today and is asking people not to come to A&E – please ring NHS111 for urgent medical advice or 999 if it is a life-threatening emergency. To ensure that all back-up processes and procedures were put in place quickly, the trust declared a major internal incident to make sure that patients already in the trust’s hospitals continued to receive the care they need.”
NHS Digital said:
“We’re aware that a number of trusts that have reported potential issues to the CareCERT team. We believe it to be ransomware.”
Hospitals have been told to pay $300 dollars – £233 – in order to regain their files and hackers are demanding this is paid in Bitcoins, an unregulated currency that authorities find difficult to track.
The attack affected Telefónica and several other large companies in Spain, FedEx and Deutsche Bahn. Other targets in at least 99 countries were also reported to have been attacked around the same time. Over 1,000 computers at the Russian Interior Ministry, the Russian Emergency Ministry and the Russian telecommunications company MegaFon, have been reported as infected.
WannaCry is believed to use the EternalBlue exploit, which was allegedly developed by the US National Security Agency, to attack computers running Microsoft Windows operating systems. ETERNALBLUE exploits vulnerability MS17-010 in Microsoft’s implementation of the SMB protocol.
Although a patch to remove that vulnerability had been issued on March 14, 2017, delays in applying security updates left some users and organisations vulnerable.
A “kill switch” hardcoded into the malware has allowed the initial infection to be halted but variants are expected to be created.


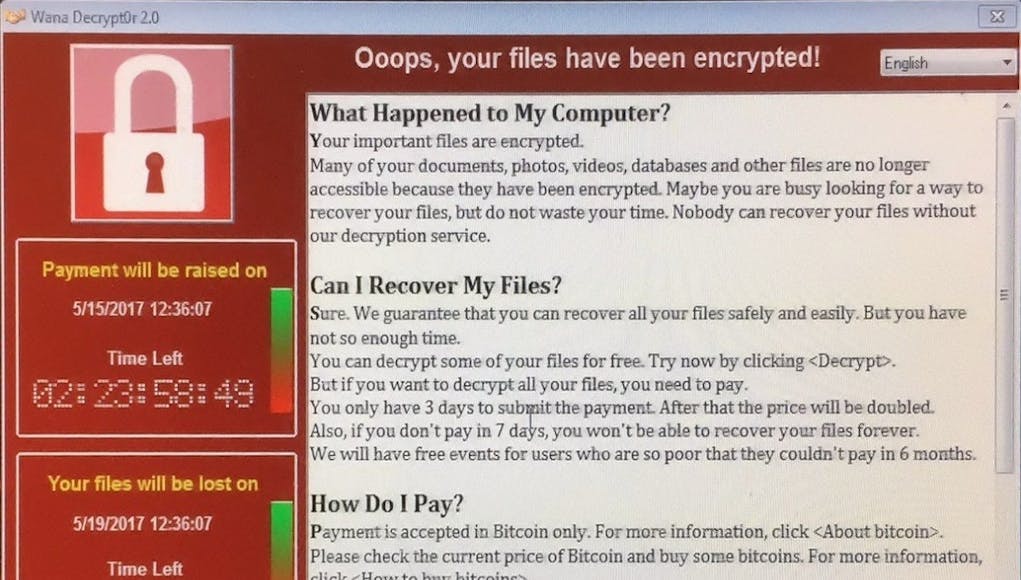







Even still, that patch to remove the vulnerability would not of been compatible with windows XP which the NHS use, Microsoft stopped supporting that three years ago.
I was using windows XP in high school nearly 15 years ago. The fact that the people tasked with saving all our lives and looking after our health are using software from 2001 in 2017 is shameful.
If you haven’t already:
(i) Run a virus scan with the latest virus definitions.
(ii) Install the latest operating system updates.
(iii) Backup your computer.
I see that Windows have now issued a ‘free’ patch. Although now no longer supporting XP, any specific historic code fault of theirs should surely be patched at any time anyway – bit late to show how easy it was now!
An attack on the NHS is an attack on the British people. This is an act of terrorism really. We should go after the punks or rouge states supporting these malicious acts.
Time to take the gloves off and stop being passive find out who they are and where they are and then drop an SAS assassination squad onto them or a brimstone missile.
Before anyone replies. I was just joking about the SAS and brimstone missiles. However we should be more assertive and go after these individuals
[…] The worry over security, in our view, isn’t really something to be concerned about. The biggest threat is experienced when submarines are in port to recieve software updates as unpatched vulnerabilities in the operating system could in theory be used by attackers to break into their systems if they were connected to the internet. However, they’re not connected to the internet and are in no way vulnerable to the type of attacks that crippled the NHS, as we reported here. […]
I don’t agree with you Mr Bell. In my opinion it is the organisations who run insecure computers that should be prosecuted. I think that the hackers are doing us a service.
Interesting perspective. Following on from that, in hindsight what the UK should really have done is for GCHQ to have launched that attack against the NHS and other key institutions itself, using the same entry and propagation tools, but with a benign payload instead of the ransomware, probably something that quietly reported back that it had penetrated such-and-such a system and left a hidden file there so that when someone went to the associated IT department and said that its security wasn’t good enough they could clearly show that something had got through.
The problem is that the white-hat hackers, at least the government ones, are hoarding exploits so they don’t want to use them in such a friendly scenario to keep them secret in case they want to do a hostile attack on a foreign state. They could still do white-hat hacking using known exploits though.
What gets me is the term “hackers” being used. Hackers are outside to in. This attack appears to be inside to outside, so it’s an infection rather than an exterior atttack.
Oh well.
[…] have taken to using the recent attacks on the NHS as part of a campaign against Trident, albeit they’ve used the wrong information. While we […]
[…] The worry over security, in our view, isn’t really something to be concerned about. The biggest threat is experienced when submarines are in port to recieve software updates as unpatched vulnerabilities in the operating system could in theory be used by attackers to break into their systems if they were connected to the internet. However, they’re not connected to the internet and are in no way vulnerable to the type of attacks that crippled the NHS, as we reported here. […]