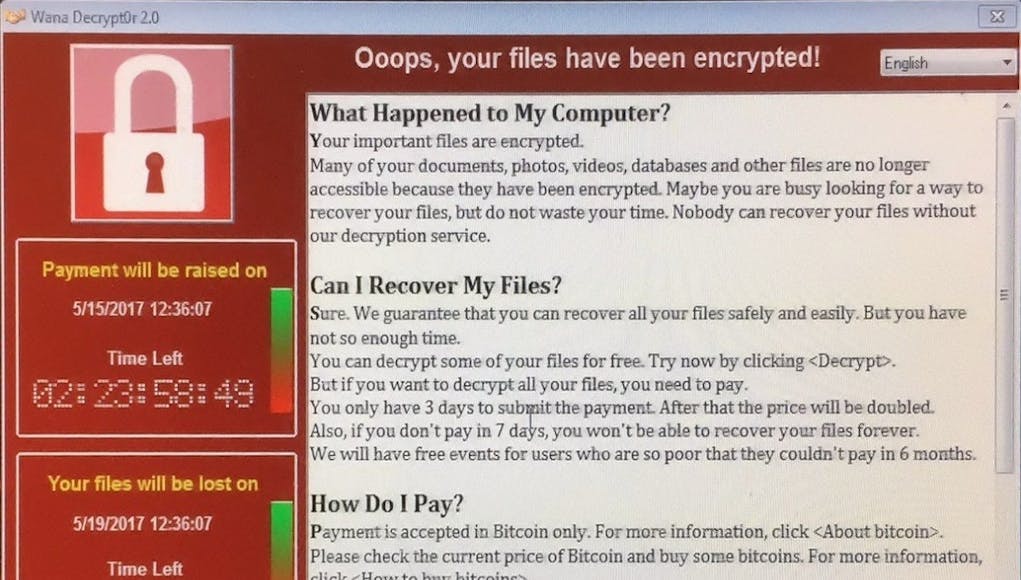
WannaCry – You’ve all heard about it, now it’s time to discover a little more about it.
The aim of this article is to provide information in a digestible manner for those of you out there that aren’t able to speak fluent “geek”, whilst still providing interesting information to those of you that are. Quite a difficult task!
What is Malware?
Malware is a portmanteau of the words Malicious and Software. It is an umbrella term that encompasses all types of malicious software e.g. Trojan Horse, Worm, Virus, and Ransomware etc. More can be read about the specific types of malware here.
What is WannaCry?
WannaCry is the name given to the ransomware and worm that encrypts the hard drive of the compromised computer and propagates around both an internal LAN and the wider internet by leveraging a vulnerability in the Windows operating system and is detailed under Microsoft Security Bulletin MS17-010.
MS17-010?
Microsoft Security Bulletin’s are used by Microsoft to release vulnerability and patching information on its software. This specific bulletin was released on 14th March 2017 relating to a vulnerability in a protocol known as Server Message Block version 1 (SMBv1). This vulnerability gained notoriety on the 14th April 2017 when it was leaked by a group of people or an individual person known as “Shadow Brokers”. This mysterious organisation has unknown aims, however they garnered the attention of the defence community by leaking over a Gigabyte of alleged National Security Agency weaponized security exploits. This specific vulnerability was given the codename ETERNALBLUE.
The vulnerability is what’s known as a “remote code execution” vulnerability which basically means that an attacker can execute commands or “code” on a victims computer without them even knowing about it or having to download any malicious files or visit any malicious links.
Sounds scary, what made this attack so successful?
To answer this I would like to split it down into 4 parts.
Part 1 – Definition of “Attack”
First of all, this wasn’t a cyber “attack”. “Attack” insinuates that it was targeted from one person to another for various aims, be they political, monetary, intellectual, or many other reasons, but the main thing to take away is that attacks are targeted. This was just a simple malware release, just like any other malware release, in the history of malware releases have been released. There is currently no evidence to suggest that anyone was targeted specifically.
Part 2 – Timing and speed
The main reason for the success of this attack was simply down to timing and speed of delivery. From public vulnerability release to full blown exploitation was a little over 2 months, which is almost unheard of. The release of the exploit by the Shadow Brokers a month after the initial patch release sped up the weaponisation phase exponentially, add the fact that the SMBv1 protocol is widely used and you clearly have a huge attack footprint for a vulnerability released not that long ago in relative terms, with an exploit already in the wild and ready to be utilised.
This effectively gave network administrators 1 month to patch a critical vulnerability, anything under that and they could potentially be compromised. Regardless of the fact that the WannaCry malware impacted around 2 months after release, it was completely plausible that someone could have used this vulnerability and exploit to infect victims much earlier.
Part 3 – System priorities
In the Cyber Security world, and indeed in the IT industry at large, there is a principle known as the C.I.A. triangle (I’m sorry to disappoint, but it’s got nothing to do with the Central Intelligence Agency). This stands for Confidentiality, Integrity, and Availability and are defined as such:
Confidentiality is similar to privacy in that you allow people to see what they’re supposed to see but assure that people cannot see what they’re not supposed to.
Integrity is that the information present is what is supposed to be present, I.e. nobody unauthorised has tampered with it.
Availability is how often a system, or some information, is available to the end user and how many different ways this information can be delivered to a user.
Now, it may surprise most of you that don’t work in IT, but availability is by far and away the dominating factor. It always has been and it always will be. Why? Because of one simple fact, what’s the point of having the most secure computer system in the world, if nobody can use it? There isn’t any. Now, “getting it right” is a difficult challenge and it requires just the right amount of each 3 aspects; a bit like the fire triangle that we are taught. However the question when asked when designing a network is nearly always “how little security can we provide, and get away with, in order to provide ‘x’ amounts of availability?”. Notice how the availability is the constant and security is the variable? That’s because businesses, in general, care most about availability.
Part 4 – Patching
Patching systems takes time. The larger and more complex the system, the more time it takes to patch. As any IT professional will tell you, all organisations have different patching schedules for different reasons, however patching an organisation the size of the NHS is incredibly difficult.
As described in part 3, almost every business is driven by availability of systems over security; and in most cases quite rightly so. Patching can have numerous unintentional consequences to that availability. For instance, how are you sure that this patch doesn’t affect all software on your network? This means patches require testing on a pre-production system before putting onto a live system. This can take days, weeks, or months. I’m certainly not absolving my fellow IT professionals from the blame, there are lazy people amongst us in all walks of life, I’m simply providing a valid reason as to why the patches may not have been applied yet, especially in an environment as availability-heavy and complex as those which are in use within the NHS.
How has the malware been delivered?
On computers there are communication channels known as “ports”. Ports are used by applications to listen for network traffic trying to connect and pass data between computers and are numbered 0-65535. SMB uses port 445.
Whilst there is no definitive answer as to how the outbreak started just yet, an increase in internet traffic on port 445 was detected prior to the outbreak, indicating a potential scan of network addresses for reconnaissance purposes. Once the reconnaissance scan had concluded, the exploit was pushed out to all devices with port 445 open, in what is likely to be a scripted (automated) process.
We know from reverse engineering the malware that this is the method used to propagate the malware around both the internet and local networks. We also know that the malware tries to establish a connection to the target for one hour when connecting over the internet and 10 minutes over a local network. If the attacker fails to connect in those time constraints, it tries a different IP address. If the connection is successfully established, the malware then propagates to the target computer, which then becomes an attacker itself.
How can organisations protect themselves?
The first port of call would be to ensure that all patches are applied at the earliest possible opportunity. As stated in part 4 earlier, this is completely dependent on your patching schedule and the risks managed by your risk owner; however I would genuinely plead for any IT professionals reading this to try and increase the speed at which your organisation patches vulnerabilities.
Secondly, ensure that any internet facing firewalls have port 445 blocked to prevent propagation from internet sources. If your network must connect to another over port 445, try to configure a Virtual Private Network connection between networks using a technology like OpenVPN or IPSEC.
Thirdly, turn off any services that are not required on your network. If you don’t have an application that requires the use of SMBv1, turn it off.
Fourthly, ensure that your organisation has up-to-date backups that are not connected via any network shares, have port 445 blocked on its software firewall, and stores several days worth of backups.
Last, do not block access to the sinkhole server (more below) which uses a HTTP request on port 80 to either of these URI’s:
iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
Ifferfsodp9ifjaposdfjhgosurijfaewrwergwea.com
What’s likely to come in the future?
The current strain of malware conducts a “beacon” on infection. If this “beacon” is successful then it doesn’t encrypt the victims hard drive and basically acts as a “kill-switch” to the malware. This was discovered by a British malware analyst that goes by the name of MalwareTech, who then purchased the domain that is the destination of the beacon and redirected it to what is known as a “sinkhole”. This has effectively killed the current strain of malware from propagating across internet connected devices; although if you block access to the domain, it will still encrypt your hard drive. It is highly likely that new strains will have different kill-switch domains, or no kill-switch functionality at all.
The current delivery method requires direct access to port 445. This limits the potentially vulnerable targets to those allowing access. It is highly likely that new strains will have different delivery methods such as e-mail phishing campaigns and malicious web links.
Clearing up some misinformation
My final section is about addressing some of the misinformation that has been spread.
Windows XP – This is a biggie. There have been numerous people trying to state that the only reason why the NHS was affected in such a way was because there were a lot of trusts using Windows XP. The fact that some trusts may be using Windows XP may or may not be true, however in this instance it is totally irrelevant. If you view the security bulletin by Microsoft, you’ll clearly see that this vulnerability affected every version of Windows to date.
Delivery Mechanism – As stated earlier, it is highly likely that new strains of this malware will be capable of being delivered in a different way, however right now, there have been no examples of it in the wild.
Evidence of underfunding in the NHS – No. While it’s obviously not recommended to continue using an unsupported version of an Operating System, there is no evidence to suggest that this outbreak would have been prevented with better funding. Many large companies were affected by this vulnerability, including, but not limited to: Telefonica, Renault, Deutsche Bahn, FedEX, Nissan, Russia Central Bank, Russian Railways, Russian Interior Ministry, Bank of China, Brazil’s Foreign Ministry, and Brazil’s Social Security System. While it may be true that some NHS trusts use Windows XP, there may be very understandable reasons as to why – cost being only one of them. Remember what was said in part 3 earlier? What if some applications do not work with newer versions of Windows? They then have to build a completely new proprietary application.
Microsoft did nothing – No. Microsoft released the patch in March for all supported operating systems. There are some people that have suggested Microsoft should continue supporting operating systems while they’re still in use in significant numbers. I disagree with this. It’s similar to saying Mercedes should have a warranty on all of their cars because some people use them outside of warranty. Further to this, Microsoft actually went out of their way to release a patch for XP that addresses this vulnerability.
Fair play to Microsoft I say.
The Russians did it – Considering that there were several Russian governmental institutions infected by this malware, it seems very highly unlikely that they will have been the originators of it.
Further Reading
If you are interested in reading into more depth about this malware, or just malware in general, please visit the following sources:
https://www.endgame.com/blog/wcrywanacry-ransomware-technical-analysis
https://blog.malwarebytes.com/threat-analysis/2017/05/the-worm-that-spreads-wanacrypt0r/
https://www.malwaretech.com/2017/05/how-to-accidentally-stop-a-global-cyber-attacks.html
Thanks
I wanted to say a big thank you to all of the contributors/writers of the above links for providing me with the information from which I produced this article.